
An end-to-end Secure Identity service that allows organizations to handle up to very large quantities of users and transactions. Starting with User Enrolment processes and continuing with Secure Validation of all kinds of digital transactions.
Powered by VERISECUP technology.
-

USER
ONBOARDING
Add users in a simple and secure
way, while fulfilling Compliance
requirements. Using Mobile
Devices, Web Portals or
Face-to-Face tools. -

USER
AUTHENTICATION
Protect Access to Systems and
allow Secure Remote Working by
Authenticating Users through
Hardware, Mobile Tokens
and Biometrics. -

TRANSACTION
VALIDATION
Securely Validate Payments
and other Digital WYSIWYS
Transactions through the use of
Mobile Devices with Biometrics
and other factors. -

DIGITAL
SIGNATURESSign Digital Transactions with
Cryptographic processes that
allow legally binging outcomes in
many regions, and with the best
User Experience.

• FULLY COMPLIANT WITH MOST REGULATIONS
All service components have been designed room the ground up to fulfill the most stringent security and compliance requirements and prevent modern and sophisticated attacks while complying with all relevant regulations.
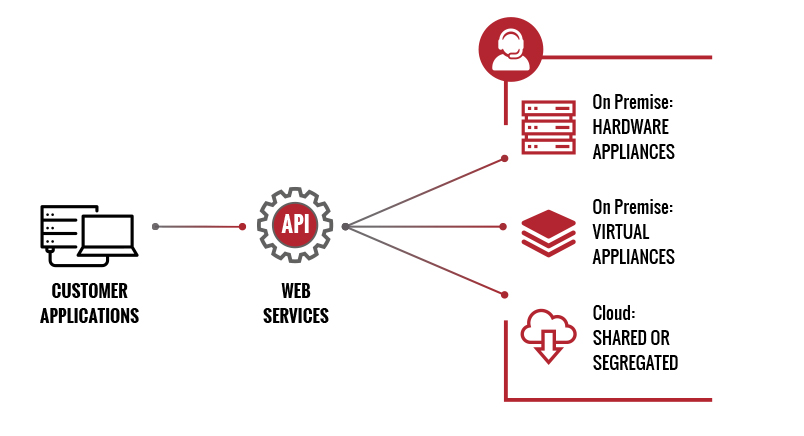
• MULTIPLE INFRASTRUCURE OPTIONS
The API can be used by various customer applications to securely validate digital transactions; and it can run on lean infrastructure at a customer’s location and/or in a remote Cloud environment, with setup and maintenance performed by VERISEC’s Expert Tech team.
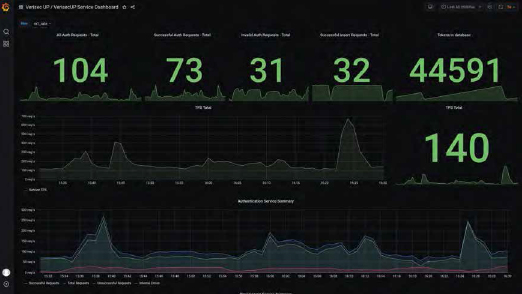
• FULL VISIBILITY SERVICE DASHBOARD
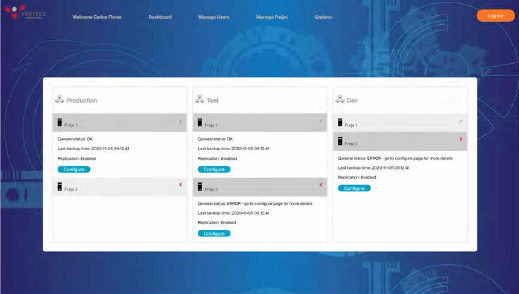
Using the VERISEC 10XAUTH Service Control Dashboard, an organization’s Security, Operation and Customer Service teams can Monitor in real-time all relevant variables related to various Authentication processes and Application environments, as well as the Service SLA itself. They can also execute day-to-day operations concerning individual users and their tokens; perform basic maintenance tasks such as setup automatic and manual backups, among others.
The Service Dashboard can also be used by organizations for current and future capacity planning for all processes and applications involving authentication. Easily identifying patterns and activity levels related to these processes, such as authentication services peak times, as well as short and long-term trends. Helping to anticipate new requirements and smoothly integrate these with current internal change processes.
CAPACITY PLANNING
SERVICE STATUS
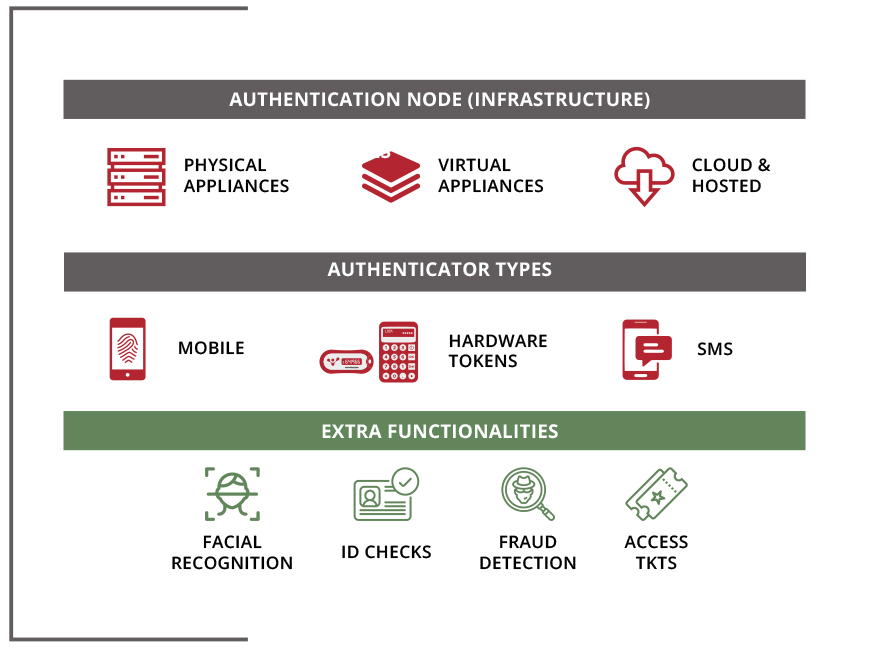
• BASED ON HIGHLY SCALABLE VERISECUP TECHNOLOGY

THE PROPRIETARY VERISECUP TECHNOLOGY ON WHICH THE SERVICE RUNS, ALLOWS FOR QUICK AND SIMPLE INTEGRATIONS WITH VARIOUS APPLICATIONS AND TO SWIFTLY SCALE UP TO MILLIONS OF USERS AND DAILY TRANSACTIONS.
VERISECUP Mobile Token App/SDK
SMS OTP delivery
Hardware Token
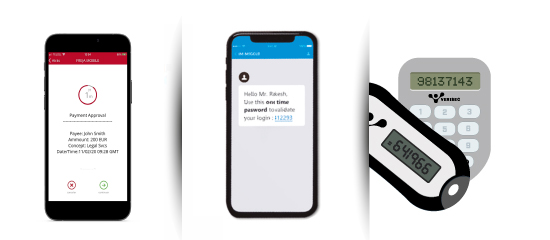
The Service’s subscription-based commercial model enables for fast user growth within predictable and controlled budgets. The VERISEC 10XAUTH Service is priced as a yearly subscription that includes all the required VERISECUP technology elements (Authentication Node- backend infrastructure in various formats, VERISECUP Mobile App/SDK) as well as 24x7x365 specialist tech support, preventive maintenance and all required integration and configuration work. All based on a total number of Active Authenticators.
VERISEC EXPERIENCED
TECH TEAM


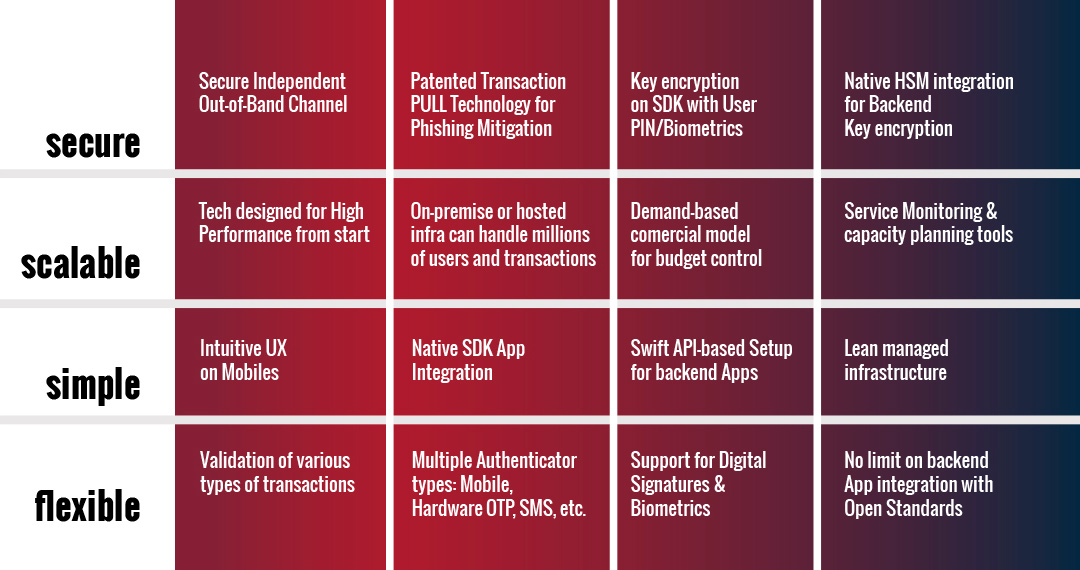
VERISEC DESIGN PRINCIPLES TRANSLATE INTO
CUSTOMER BENEFITS
WHAT YOU GET WITH THE VERISEC 10XAUTH SERVICE
THE LATEST TECH TO SCALE UP
• Designed from scratch to handle up to millions of users and Transactions using a lean infrastructure.
• No Capex or obsolescence risks involved and ability to smoothly handle any activity peaks.

THE LATEST TECH TO SECURE

• At the client level, patented SDK uses Secure Channel with PULL process to pass keys and transaction data.
• At the server level, all security key material stored within hardware security modules.
THE EXPERIENCE & TALENT
• VERISEC’s experienced Tech team can swiftly configure service components to cater for each organizations ongoing needs.
• No learning curves or training required & no staff rotation risks.

THE PEACE OF MIND

• VERISEC’s Tech team will make sure service components are in optimum condition for best performance & security levels.
• Control & Full Visibility over all service aspects for ops and sec teams.


10XAUTH
In a time of constant Cyber Attacks where user credentials and passwords are in most cases either the target or the means for the attacks, Security and Regulation requirements demand the use of Strong User Authentication applied to an ever-growing number and types of users and transactions. For many financial institutions particularly, when it comes to authentication, SCALE is the new name of the game. However, this exponential level of growth is not best handled by Authentication Systems that can only grow in a “normal” way. This level of growth requires an Authentication System that can grow 10 times as fast & 10 times as big, that allows organizations to GO LARGE & SCALE UP.



